Infographic: Why Vendor Cybersecurity Is The Next Big Supply Chain Topic
The issue of vendor cybersecurity isn't new, but awareness of the risk involved has been growing steadily. Let's take a look at why supply chain cybersecurity is important and how businesses can best mitigate risks.
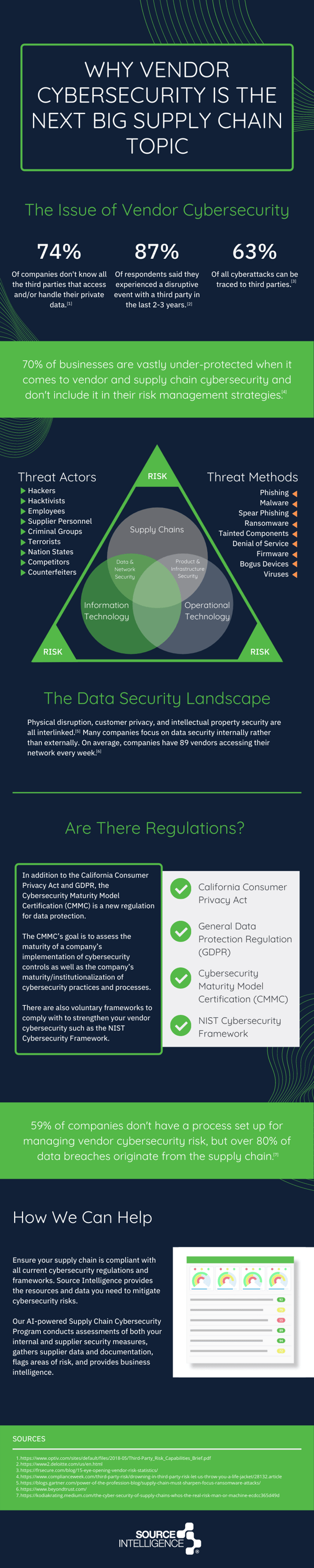
The Issue of Vendor Cybersecurity
70% of all businesses are vastly under-protected when it comes to vendor and supply chain cybersecurity and don't include it in their risk management strategies according to a report by Compliance Week. This leaves many companies vulnerable to cyber attacks, particularly through their third parties and suppliers. According to FR Secure, 63% of all cyberattacks can be traced to third parties, and 87% of companies have experienced a disruptive incident with a vendor in the last 2-3 years.
Much of vendor cybersecurity risks stem from a lack of transparency. Optiv reported that 74% of companies aren't aware of every third party that has access to or handles their private data. In addition, many companies aren't aware of how many vendors are accessing their networks, which on average is 89 per week.
The Data Security Landscape
Physical disruption, customer privacy, and intellectual property security is all interlinked. For a successful risk management strategy, supply chain, information technology, and operational technology must be taken into consideration. Many companies focus only on one or two, which leaves the entire structure vulnerable.
When it comes to vendor cyber attacks, some of the common threat actors include:
- Hackers
- Hacktivists
- Employees
- Supplier personnel
- Criminal groups
- Terrorists
- Nation states
- Competitors
- Counterfeiters
Some of the common threat methods include:
- Phishing
- Malware
- Spear phishing
- Ransomware
- Tainted components
- Denial of service
- Firmware
- Bogus devices
- Viruses
It's crucial to make a plan of action to prevent against all these common actors and methods.
Are There Vendor Cybersecurity Regulations?
In addition to the California Consumer Privacy Act and GDPR, the Cybersecurity Maturity Model Certification (CMMC) is a new regulation for data protection.
The CMMC’s goal is to assess the maturity of a company’s implementation of cybersecurity controls as well as the company’s maturity/institutionalization of cybersecurity practices and processes.
There are also voluntary frameworks to comply with to strengthen your vendor cybersecurity such as the NIST Cybersecurity Framework.
How Source Intelligence Can Help
We give businesses the data and resources you need to ensure your supply chain is compliant with all current cybersecurity regulations and frameworks. Our AI-powered Supply Chain Cybersecurity Program conducts assessments of both your internal and supplier security measures, gathers supplier data and documentation, flags areas of risk, and provides business intelligence.
Request a demo to see how our cybersecurity program can strengthen your supply chain risk management.



